The Microsoft Calling Scam
Have you ever heard of the Microsoft Calling scam which was a hot story in the news a few months back? If not, let me tell you what it actually is. A person calls you and asks for you by naming you posing as computer security pros from legitimate companies, companies such as Microsoft as you might be using Windows. The fake computer expert asks you to open your Command Prompt Window and asks you to type some commands in it about which you might have no idea and also download some sort of Malware. If you do it, you are in deep waters. After this, you would be asked for your Credit Card number for an invoice or may be something else.
This could cost you $875 in stolen money and as much as $4,800 in computer repair bills to undo the damage.
Common scams that use the Microsoft name
- Someone from “Microsoft Tech Support” calls to fix your computer”
- You have won the Microsoft Lottery
- “Microsoft” requires credit card information to validate your copy of Windows”
- “Microsoft” sends unsolicited email messages with attached security updates
Find if Your PC is Infected
If you have been a victim of any such scam or even a Facebook Scam (see example) you need to follow the steps listed below which would help you know if your computer is really infected or not.
Check Your Browser Extensions
Some scams on Facebook ask you to install an extension on your browser due to which you can see links posted on your friends’ wall from your account. What about the authentication? They really don’t need it. The cookies stored in your browser does the job. In such cases you can uninstall the extension and be sure to have a look at the URL before you download anything. These spammers usually make use of free services like Blogger.com or Weebly.com report it to them when you see such scams.
Check Active Connections on Your PC
If you do not see any extension installed and your PC is not behaving normally, you are perhaps connected to someone else at a different place without your knowledge. The downloaded malware sets up a connection to the hacker from your PC and hence transmission of personal data takes place. These malwares could possible be Keyloggers which record each and everything you type on your keyboard and send it to the hacker. These Keyloggers can also send screenshots of the screen to the hacker in regular intervals. If you are doing an online transaction, your card number and PIN are at stake. Avoid such things and call up a friend asking him/her to change your passwords.
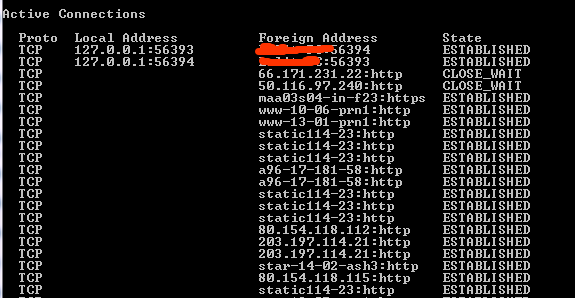
To check connections on your PC, you need to Go to Start->Run->cmd Alternatively, go to Start->Programs->Accessories Right click on Command Prompt and choose “Run as Administrator”. In the command prompt window, type netstat and hit Enter. Don’t be shocked to see a lot of lines. These lines tell you the location your PC is connected to though it might take a few seconds for the whole list to be populated.
The window has three columns now which is Proto, Local Address and Foreign Address. The Proto must be TCP. If the local address is an IP address which can either be 127.0.0.1:”Port” (“Port” can be any number, we are concerned about the IP address) or the IP address of your Internet Service provider. If you are on a WiFi connection, the IP address would be of that connection which you would see is repeated a lot of times.
The Foreign Address is again an IP address with a Port number. But how do you know which location this IP address represent? Just head over to http://www.ip-adress.com/ip_tracer/ and enter the IP address over there to see where the IP address points to. But you can also see many Foreign Addresses which are not in the form of an IP address. Many legitimate online companies use obscure domain names for connections that are never usually seen by end users. We need to turn those foreign IP addresses into readable names which can be done using the netstat -f command. When you do this you see a longer list which displays the domain names in the foreign address column. A few more IP address might belong to the applications on your PC which are connected to a server via the Internet.
Check Which Program is Connected to the Internet
To view the applications or programs which are installed on your PC and connected to a server via the Internet, you need to type netstat -b. Now you would see the name of all the applications in the left most column as [program]. In this way you can see all the applications which are connected to some other location via the internet. When I did this, I could find a few applications like Chrome.exe, Skype.exe googletalkplugin.exe in the left. If you find something unusual, you need to find out what it is. Read on to know what it is:
Check if the Program is Safe or Not
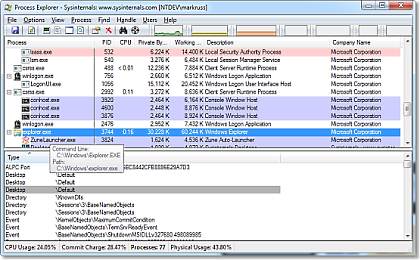
So you find out a process which you are not familiar with. In this case I recommend you to download Process Explorer which requires no installation. Process Explorer shows you information about which handles and DLLs processes have opened or loaded.
Using Process Explorer you can find out more about the active connections. It displays the name of the company the active processes are connected to. Most of them would be Microsoft Corporation or perhaps Google Inc if you are using Google Chrome. A few more processes might be running which check for software updates. If those are unnecessary, right click and choose Kill process.
Coming back to the unfamiliar process. If you suspect it’s a malware, right click on it and choose Search Online. This will make the process to be searched in the default search engine of your default browser. With the help of search results, you can see what other people have to say about the process. If you see some negative comments about that process, your computer might be under attack.
Running Belarc Advisor (Free)
You can always go to the Control Panel and check for installed programs and updates. If something unknown or suspicious has been installed, remove it. But have you heard of Keyloggers? These are programs which get installed on your PC and can record whatever you type on your Keyboard and send it to a Hacker’s email address. Apart from this, it can also send a screenshot of your Computer screen to the hacker. The keyloggers run in background and it is impossible to trace out a keylogger as it does not appear in the task manager or in the Installed programs window in Control Panel. Moreover, a hacker may even create a user account in Windows. There are many such possibilities and in that case I recommend running Belarc Advisor. The Belarc Advisor builds a detailed profile of your installed software and hardware, network inventory, missing Microsoft hotfixes, anti-virus status, security benchmarks, and displays the results in your Web browser. It is one of the best tools to find complete information about your PC.
The next post on this blog would be about how to recover from such an attack, so stay updated.
You can check my post on how to recover from Hacking Attack.